In two influential articles in June 2016, immediately following the Crowdstrike announcement, SecureWorks (June 16 here and June 26 here) purported to connect the DNC hack to a 2015-6 phishing campaign which they attributed to APT28. SecureWorks identified two malicious domains in their article. In today’s article, I’ll show that infrastructure from one domain are connected to domains identified as APT28 in early literature, while infrastructure from the other domain leads in an unexpected direction.
SecureWorks Phishing Examples
SecureWorks showed two examples of phishing emails in their June 26, 2016 article, both taken from 2015. A distinctive feature of this phishing campaign was the use of bitly links to further camouflage the typosquatting domain.
accoounts-google.com
Their first example was taken from phishtank.com incident reports 3160712 and 3160715, the first asking about a bitly link and the second from the expanded phrase which linked to accoounts-google.com, a malicious typosquatting domain.
|
|
|
|
The full syntax of the expressions is not shown in the SecureWorks figures, but, for completeness, is shown below. First, here is the expansion of Bitly 1PXQ8zP+ (presently marked by Bitly as malicious) and the full expression in phishtank.com incident 316-715:


The malicious address contained a webpage exactly emulating a Gmail log-in page at which the target would be invited to enter credentials, after which he would be transferred to his actual login page. Meanwhile, his emails would be harvested by the hackers more or less immediately without him knowing.
Phishtank incidents 3160712 and 3160715 were submitted by user aksana (metadata chopped off in the SecureWorks figure), who was, by coincidence or not, involved with InformNapalm, a Ukrainian hacking group followed by Dmitri Alperovitch of Crowdstrike.
googlesetting.com
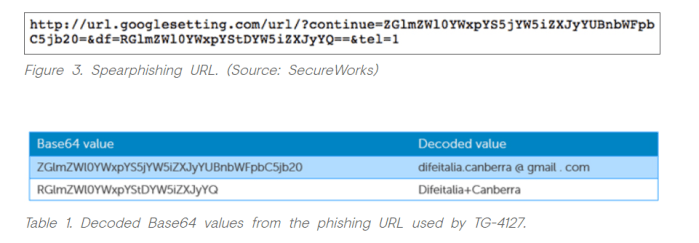
Their second example used a different typosquatting domain (url.googlesetting.com) but otherwise nearly identical syntax to the unpacked Bitly expression shown above (url/continue=*&df=*&tel=1)
|
|
In this case, the first parameter in the expression (YZGlmZ…) is the unencrypted base64 expression for the gmail address of an attache in the Embassy of Italy in Australia.
Registrant Email Addresses
googlesetting.com
SecureWorks didn’t discuss how it attributed the SW-2015 phishing campaign to APT28. However, there is an obvious connection via registrant email for googlesetting.com, of which url.googlesetting.com is a subdomain. Its registrant, andre_roy@mail.com, is also registrant for numerous domains in the October 2014 PWC inventory of APT28 domains. This is nicely shown in the ThreatCrowd connections graph for url.googlesetting.com, shown below. The two domains, registrant email address are highlighted, as well as two IP addresses (58.158.177.102 and 37.221.165.244), which, for now, are Easter eggs. All the domains linked to andre_roy were previously identified as APT28. Seems pretty convincing. accoounts-google.com
accoounts-google.com
However, registrant and registrant email address for the other phishing domain accoounts-google.com leads in a different and unexpected direction. A standard Whois lookup for at whois.icann.org yielded registrant Gennadiy Borisov in Varna, Bulgaria, together with registrant email of yingw90@yahoo.com, screenshot reproduced below.
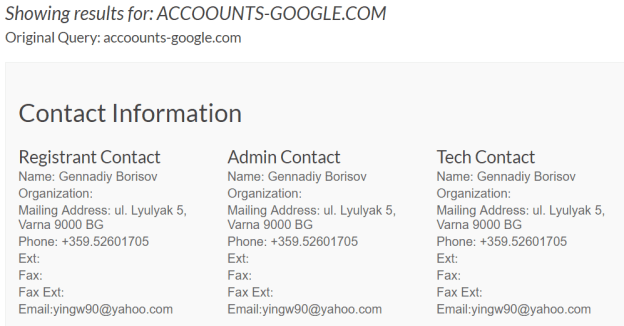
In the prior post on the Lurk Banking Gang, Gennadiy Borisov and yingw90@yahoo.com were registrar and registrant email of dozens, if not hundreds, of crimeware domains associated with the Angler exploit kit. (This unexpected appearance of yingw90 is the “Easter egg” promised in the preceding post).
In other words, one of the domains (accoounts-google.com) in the SW-2015 phishing campaign appears to connect just as strongly (registrar and registrant email) to the Angler malware group as the other domain (url.googlesetting.com) connects to the APT28 malware group.
Discussion
APT28 (Fancy Bear) is characterized in computer security literature as a presumed unique hacking group which uses characteristic malware: Sofacy, Chopstick and Eviltoss (or variations thereof, with names varying in the literature). It is characterized by resourcefulness and ingenuity in developing zero-day exploits to deliver the malware. It is usually said to be narrowly focused on defence and government sectors. Two of its most popular delivery methods are a malicious attachment to a document delivered by email or a link to a malicious page of topical interest which downloads malware in the background.
On the other hand, phishing (and credential theft through phishing) is one of the most common and commonplace forms of cybercrime and difficult to attribute. In late 2014, Google researchers examined thousands of phishing incidents, observing that credential theft was used to “send spam, to tap into the social connections of victims to compromise additional accounts or alternatively liquidate a victim’s financial assets”. They reported that “phishing requests target victims’ email (35%) and banking institutions (21%) accounts, as well as their app stores and social networking credentials”. In the hijacking cases that they analyzed, they found that “most of the hijackers appear to originate from five main countries: China, Ivory Coast, Malaysia, Nigeria, and South Africa”. In late 2014, a computer security analyst, commenting on the Google article, showed examples of typical gmail phishing emails and webpages, noting that they had seen “400+ Google-related phishing URLs” in the previous week:
These just a few examples of the “look and feel” of some of the 400+ Google-related phishing URLs we’ve seen in the past seven days at Malcovery security. Most of them were seen many times each!
The phishing webpages in the 2015-2016 phishing campaign of interest to SecureWorks (the “SW Phishing Campaign”) were no better and no worse than others in the genre.
To my knowledge, there have been no reports of installation of distinctive APT28 malware on the targets of the 2015-2016 phishing campaign studied by SecureWorks (the “SW Campaign” for short). Instead, it was an entirely commonplace attempt to steal credentials, indistinguishable in structure from thousands of similar attempts to steal email, banking and other credentials. It specifically targeted Gmail credentials, which together with Yahoo and Microsoft credentials, are the most popular forms of credential theft. Such campaigns frequently use domain names which “spoof” or “typosquat” the legitimate names – there is nothing distinctive to APT28 or even Russia in that technique. It could be Nigerian or American, just as easily.
Attribution of the phishing campaign to APT28 was therefore done on the basis of infrastructure connections. But while there is an infrastructure association to APT28 but there is also an association to a prominent crimeware gang.
From this, I’m beginning to question how “APT28” is defined and attributed. On the one hand, one sees incidents in which Sofacy and Coreshell/X-Agent are dropped into computers using sophisticated zero-day exploits – these seem useful attributions. On the other hand, one sees incidents of commonplace credential phishing without accompanying Socacy, Coreshell malware, which are attributed by supposed chains of infrastructure e.g. registrant email address or common IP address going back to incidents as far back as 2014, not necessarily well documented. As an outsider to these attribution arguments, this latter class of attribution seems to me to require lower confidence. If information is contradictory, then I don’t see how much confidence can be attached at all.






54 Comments
Interesting, my view is that the view these phishing campaigns targeted accounts viewed of intelligence values may be a result of cherry-picking. From memory it results from a dataset of around 14000 bit.ly links supplied representing 3000 targets (presumably by law enforcement or intelligence) to a cyber-security firm.
However, these phishing campaigns are going to be high volume and low success rate affairs. Suppose you successfully phish some who goes to the same church as Colin Powell, your next rounding of phishing is going to include all the email addresses in this person’s address-book. Then suppose Colin Powell is one of the few people tricked by the phish link. Then the next round of phishing is going to be highly enriched with military and political addresses from Colin Powell’s address book – it is going to LOOK like an intelligence campaign, particularly if the bit.ly links dataset is only a subset, but it isn’t.
One caveat is that the phishing technique is fairly simple to copy – bit.ly links in base64 and variant account urls. Multiple actors could be using it.
The other caveat – don’t assume the phishes have any connection to the Podesta emails ending up at Wikileaks. Leakers may have just waited for the first convenient phishing attempt to arrive and used that as a convenient cover to leak.
Secureworks quantifies their attribution as “moderate confidence”: they base it mostly on the nature of the targets attacked plus similar techniques being used.
So if many black men were victims plus all shot than Secureworks is moderately certain this was done all by the same single perp – THE serial killer.
I wouldn’t want Secureworks as judge or jury anywhere.
Antony, I believe you have identified the fundamental evidence of bias. To ignore that criminals take advantage of opportunities created by the presence of other suspects is a clear indication of non-professional crime analysis.
dcleaks.com –> whois –> Shinjiru Technology
shinjiru.com –> 185.148.146.211.
185.148.146.211. –> GeoIP –> Bulgaria –> BelCloud Hosting Corporation
One possibility is that dcleaks.com may have been sold/taken over by “the Bulgarian group”, after the US election to be turned into the phishing outfit it is now.
Or it may have been under the same ownership all the time.
The nameserver for dcleaks.com, ns1.piradius.net (owned by shinjiru) was last changed Tue, 22 Mar 2016 15:10:38 GMT
Piradius.net seems to be exclusively hosting dodgy sites.
See more stuff on my blog here: https://loadedforguccifer.wordpress.com/2018/02/10/dcleaky/
classic APT28 site adobeincorp.com (but probably non-Sofacy) turns up in riskiq.com search of
130.255.184.196, one of the hardwired IP addresses in DNC XTunnel version
https://community.riskiq.com/search/130.255.184.196
It was originally connected to your favorite Nobby Beach, also connected to orderbox-dns

Agree & nice find 🙂
Here is another example. Remember this article by Threat Connect?
2016-06-17 Rebooting Watergate: Tapping into the Democratic National Committee
But there is an issue with this conclusion: 5.135.183.154 is indeed a parking server, but one for a dubious provider of bitcoin hosting, not APT28 / Fancy Bear.
Just look at these reports on ThreatCrowd: https://www.threatcrowd.org/domain.php?domain=misdepatrment.com
NameServer A8332F3A.BITCOIN-DNS.HOSTING
Created & parked at 5.135.183.154 around 2016-03-25, moved to 45.32.129.185 in 2016 just before hack.
Let’s check that parking server (5.135.183.154) using https://www.threatcrowd.org/ip.php?ip=5.135.183.154
This is a typical parking server for newly created IP names, it has (had) loads of names, many of those suspicious and probably malicious.
Clearly this is a parking server but not for some APT, but more for all kinds of cyber-criminal purposes.
One of the related names for 5.135.183.154 is: NS2.DOMAINS4BITCOINS-PARKING.COM
For reference below the details for the related X-Tunnel binary reported by CrowdStrike as having been found at the DNC.
SHA-1: f09780ba9eb7f7426f93126bc198292f5106424b, SHA256: 4845761c9bed0563d0aa83613311191e075a9b58861e80392914d61a21bad976
Compilation Timestamp 2016-04-25 10:58:38
IP addresses: 45.32.129.185, 130.255.184.196, 176.31.112.10
The subsequent IP addresses for misdepatrment.com similarly host a zoo of crimeware. I’ve got notes in inventory on this.
Following subseuqnt history of actblues.com, another contemporary site, is similarly interesting.
Beware of tunnel vision. Crimeware will just go to cheap readily available IP addresses, as will anyone who just wants a very temporary parking spot for a domain. You are zeroing down on crimeware because that is all that gets reported.
Phishing is high volume, low success. MIS department is a small firm just of IT professionals. Even IT professionals can very occasionally fall for a phish, but it is only going to be very occasionally. What we are seeing is a very percentage of MIS or ex-MIS employees seemingly being fooled by very straightforward phishes
Wikileaks have always said these were leaks, misdepatrment.com could just be a way for someone to appear to lose their credentials so they can leak without being caught. It might not be impossible to find out what misdepartment.com change password page looks like, but the best placed persons to do it would be MIS or ex-MIS department employees.
I have copy of it from archive.org.
OK, but the firm is tiny
http://web.archive.org/web/20150906065827/http://www.misdepartment.com/staff
Remember you not just have to grab credentials, you have to grab credentials of someone with worthwhile privileges.
“Enter your The MIS Department, Inc. username.” this isn’t going to be for any normal DNC user. All I am saying is you should consider the possibility that someone faked a break-in in order to leak. And yes, ignore the reported malware, I am sure it was genuinely found, just not related to DNC emails.
Just for interest, after June 2016 the website pulled its staff profiles page – so we can’t work out who might have got the chop.
MIS-operated helpdesk active in DNC Wikileaks archive right up to the end on May 25, 2016.
it’s not just the Staff profiles page – it’s every page in the MIS website. At almost exactly the same time as CrowdStrike moves in on DNC and makes announcement of “Russians”, Rajeev Chopra seems to have gone on a walkabout and MIS appears to go out of business. Chopra was big Bernie supporter, as were MIS. Lots of motive and opportunity for email hack ~May 25.
and yet, I’ve never seen a single interview of anyone with MIS. Wonder if FBI or Mueller ever talked to them.
I had looked at 5.135.183.154 at threatcrowd. The connections graph looks clean/ I completely missed its role as an incubator site. I looked at the connections graph for one of the other incubated sites, semi at random, but its name, windowsdefenderupdater.com, is reminiscent of a canonical “APT28” site. In its future is malware site 209.99.40.223 – also in the future of misdepatrment after 45.32.129.185.
Here is connection graph of 209.99.40.223 – bristling with crimeware.

Reminder to self: show relationship to 176.31.112.10.
Aye, and look not just at the chart look at the very long list at the righthand side.
Or look via RiskIQ at formerly associated IP names, ie previously parked domains.
Just a glimpse at the long list of names should suffice. Many or most can only have been used for all kinds off malicious purposes…
Reblogged this on I Didn't Ask To Be a Blog.
On August 2nd 2016 Microsoft filed a case against “Strontium’s” (= ) use of spoofed domain names – a legal tool to combat this practice
Examples above like http://www.windowsdefenderupdater.com or windowspatchmanager.com give them a legal foot hold.
Click to access cmplt.pdf
“Eventually, Microsoft used the lawsuit as a tool to create sinkhole domains, allowing the company’s Digital Crimes Unit to actively monitor the malware infrastructures and identify potential victims.”
From personal experience with Microsoft update & patch policies and practices I must say life is still frustrating for legal users. Four BSODs last week on a Windows 10 based server due to this – in 2018, not 1998. Many will forgo these “patches” therefore.
Why is this topic on CLIMATE audit?
Hans, your question is broad but I take it to mean why does this blog stray from focusing posting exclusively on climate science related papers. To this I offer the following:
1) Climate Audit is an amazing free to user establishment created by its proprietor after his retirement from surely equal level workload for pay. If one cannot have independence to focus their time as they please what is the point of retirement?
2) However, whereas Climate Audit is an amazing archival resource with historical value, and is the product of contributors as well as the proprietor, is there not some higher public obligation for the preservation of its content as well as its brand?
3) What are the options available to the proprietor of such a blog should they desire the continuation or at least preservation of their blog?
4) If the proprietor decides to utilize the blog for investigations unrelated to climate but of other items of his interest should the followers who are not interested in those topics protest? If so, should the protest be a simple non-participation or and announcement of displeasure or active disruption? I don’t know, especially if one has been a decades-long active contributor.
Hans, thank you for your years of contribution going back to the early years to present. And I apologize for weighing my interest in Steve’s off-topic posts more than to the obligation of putting pressure for the preservation of the Climate Audit brand, which you are a part.
Ron I do not endorse what is happening in the brands name. Steve, I think you better should have bought a new domainname for non climate related topics. My five cents…
Is the brand Steve McIntyre or Climate Audit, or both?
Honestly, it’s less the posts on the site than the twitter feed. Obviously, it is up to Steve Mc what he chooses to write about, but I wish I didn’t know that what he really wants to write about is anti-US, pro-unrepentant KGB hack, pro-genocidal dictator conspiracy theories.
But w/e – you take the good with the bad and you engage on the level of facts, I guess..
Because it is Steve McIn’s site and is more “climate AUDIT.
He also audited “NFL Officials Over-Inflated Patriot Balls” before https://climateaudit.org/2015/06/28/the-referees-over-inflated-patriot-balls/
Also some mayor developments go fast, like the sudden post-HRC Russiaphobia of US deep state, or even faster: the chemical attack narratives in the UK and Syria recently. Too fast to set up new sites for every Audit.
Those who warn about a climate Armageddon in a few decades should be concerned even more about a nuclear Armageddon in a few days (Syria).
“Is the brand Steve McIntyre or Climate Audit, or both?”
Steve definitely owns it and is a major part, but the brand was also built by the quality of contributors.
Newsaudit.org is taken by a cyber-squatter but many other variations are available for as little as 2 bucks, like newsaudit.today.
Steve, now that the DNC has sued the GOP, the Trump campaign and others for this hack, does this analysis take on new life? I would think it would be in the defendants’ interest to get to the bottom if what actually happened, given that plaintiffs are likely just accepting CloudStrike’s conclustion on their face? What do you think? Are you going to be an expert witness?
Steve: FWIW, someone named Sara Carter is reporting that the House Intelligence Committee has identified James Clapper as the source of the leak to CNN about Comey’s briefing Trump on the Steele Dossier. Others are repeating her claims. The story has reached Breitbart and the Washington Times, but not the MSM. Clapper became a consultant for CNN after he left government.
http://www.thegatewaypundit.com/2018/03/sara-carter-james-clapper-allegedly-leaked-information-trumps-classified-briefing-phony-dossier-cnn/
You wrote about this subject here:
Respectfully, Frank
All over Fox News Channel. Sara Carter should get a Pulitzer. Pencilneck Adam Schiff seems to have an informal CNN slot.
For the timeline of the (non )investigation of HRC’s private e-mail server this FOX April 10th 2016 interview is interesting: US president Obama proclaims publicly that he believes that HRC was just careless with e-mails – she didn’t jeopardize national security (~9 min in). He didn’t send a directive to his DOJ or the FBI; he didn’t have to anymore after this.(< 6000 views) https://www.youtube.com/watch?v=xertY_yvu2k
When Trump talks similar he gets lynched in the MSM and that video will go viral.
Steve: I see that Mueller has named another dozen or so Russian agents involved in various computer activities intended to influence the 2016 election and sow dissension, especially hacking Does any of this new information impact your position that the forensic evidence related to Russian involvement was ambiguous? Bringing an indictment presumably implies stronger evidence that issuing an intelligence report. In theory, it is legally unethical for a prosecutor to bring charges knowing his evidence will be easily refuted in court.
Respectfully, Frank.
Frank, please look at the timing of Mueller’s new indictment: released on July 13 th 2018, so 3 days before US president Donald Trump’s meeting with Russia’s president Vladimir Putin in Helsinki.
http://apps.washingtonpost.com/g/documents/national/read-mueller-probe-indictment-of-12-russians-for-hacking-democrats/3087/
US deep state wants to keep their biggest foreign bogeyman vilified, as that is the mainstay of their ever increasing requests for more funds. Peace = less money/ power for them.
NSA /CIA directed personnel involved in foreign hacking is now exposed to tit-for-tat criminal cases against them abroad. Germany’s Chancellor Angela could start for them hacking her personal mobile phone.
Of course they count on not being caught like those 12 Russians on their own CCTV by the Dutch…
Antony: I’m not interested in the timing to the announcement. I’m interested what Steve thinks about the new information that has become available since he wrote this post.
Trump approved the timing, not some “Deep State”
https://www.bloomberg.com/news/articles/2018-07-17/trump-said-to-decide-russia-indictments-should-come-pre-summit
You are certainly entitled to your own opinion, but if Mr. Trump were to call Putin the “biggest foreign bogeyman” of the “US deep state”, that might result in charges of treason and renewed calls for impeachment – even from some Republicans. The same factors made that prompted Putin’s intervention in Ukraine – Russians left outside the borders when the USSR disintegrated, Putin’s desire to recreate the Russian empire – are a major problem in Baltic States that are part of NATO. Those same factors motivated Hitler in the 1930’s. So the “Deep State” I’m most worried about it Putin’s.
Deputy Attorney General Rod Rosenstein went to Trump last week and offered him the choice: before or after the Putin summit on Monday in Helsinki? Trump chose before
So Trump was given the choice between a rock and a hard place by Rosenstein.
While you are worried about Russia’s deep state, Daily Caller is more worried about the Brennans, Clappers and Comeys of the land of the brave and “the home of the free”: http://dailycaller.com/2018/07/19/trump-has-been-set-up-framed-and-relentlessly-persecuted-by-the-american-intelligence-community/
Frank: And you are entitled to your opinion, but your “presumptions” that Mueller and his team are concerned with disbarment or any other consequence for their misconduct is hilariously naive. Just one example- After Hillary left State Dep’t, a foia action was brought in 2012 to get her State Dep’t emails. After two years of obfuscation State Dep’t lawyers succeeded in dismissal because they told a fed judge that there were no records existing. After Hillary’s presser on the steps of the UN bldg in May ’15, (when she admitted to holding gov’t records for all that time)(another charge Mr. Comey ignored), the fed judge re-opened the case and oversaw the slow-motion release of “public records”. For lying to fed judge, what consequence? Please tell me I’m wrong, and show me where somebody was disciplined, even reprimanded.
Other examples abound, won’t bother listing them. Point is, right now (in the example you cite), Mueller is withholding discovery in criminal case on a basis (Defendant must prove it will show up?!) not found in any rules.
I won’t pretend to answer for our host, but my answer to your question is, Mueller seems to be following all the lemmings by relying on Crowdstrike. I hope one of the D’s in this new case files a plea and gets discovery, even a trial, because from what we see in previous threads, these attributions will not be supported by evidence beyond Crowdstrike bogus attribution. If you think one or more of our intel agencies confirmed Crowdstrike, then ask your source when that intel agency(s) had possession of DNC server.
Maybe I should be happy that someone still has faith in these folks, Mueller and his team do not deserve your faith.
Paul Courtney: A link to: “Asking for Trouble: When Lawyers Lie to Judges” https://www.stroock.com/SiteFiles/Pub784.pdf
I’d say that the email scandal shows that our system takes these ADMINISTRATIVE legal procedures seriously – though legal procedures can be slow. And it takes CRIMINAL legal procedures more seriously.
One reason the process took so long was that the DoS, not HRC, was responsible for responding to FOI requests. They grossly failed to maintain the necessary records.
You write: “Maybe I should be happy that someone still has faith in these folks, Mueller and his team do not deserve your faith.”
I think we should all consult a variety of sources and our common sense before deciding who and what to believe in. CONFIRMATION BIAS makes it very difficult to learn and retain facts that disagree with our personal biases.
Not understanding the failure to prosecute HRC, I listened to Comey’s testimony to Congress and how he answered Republican questions.
There has been a politically-motivated explosion of news about both real and imaginary problems at the FBI. However, no one in the Intelligence Community confirmed or even leaked the existence of an investigation into the Steele Dossier before the election and unleashed the storm of stories that appeared in January 2017. I personally find it impossible to believe in a grand anti-Trump conspiracy when it would have been trivial to prevent his election.
FWIW, Mr. Mueller is entitled to keep the results of his investigation secret until he has finished questioning all of the witnesses – so he was some way to assess credibility. Mr. Trump hasn’t been interviewed yet. Congressional demands for “all records” conflict with the DoJ’s investigation. Congress can conduct their oversight AFTER Mr. Trump is interviewed.
Paul Courtney: A link to: “Asking for Trouble: When Lawyers Lie to Judges” https://www.stroock.com/SiteFiles/Pub784.pdf
I’d say that the email scandal shows that our system takes these ADMINISTRATIVE legal procedures seriously – though legal procedures can be slow. And it takes CRIMINAL legal procedures more seriously.
You write: “Maybe I should be happy that someone still has faith in these folks, Mueller and his team do not deserve your faith.”
I think we should all consult a variety of sources and our common sense before deciding who and what to believe in. CONFIRMATION BIAS makes it very difficult to learn and retain facts that disagree with our personal biases.
Not understanding the failure to prosecute HRC, I listened to Comey’s testimony to Congress and how he answered Republican questions.
If there were a grand conspiracy against Trump in the FBI/DOJ, the existence of an investigation into the Steele Dossier would have been confirmed or leaked before the election, unleashing the storm of stories that appeared in January 2017.
FWIW, Mr. Mueller is entitled to keep the results of his investigation secret until he has finished questioning all of the witnesses – so he was some way to assess credibility. Mr. Trump hasn’t been interviewed yet.
Paul Courtney: A link to: “Asking for Trouble: When Lawyers Lie to Judges”
Click to access Pub784.pdf
Paul: I’d say that the email scandal shows that our system takes these ADMINISTRATIVE legal procedures seriously – though legal procedures can be slow. And it takes CRIMINAL legal procedures more seriously. After a defendant appears in court, pleads not guilty and posts bond guaranteeing his appearance, then the defendant can demand to see the evidence against him.
You write: “Maybe I should be happy that someone still has faith in these folks, Mueller and his team do not deserve your faith.”
I think we should all consult a variety of sources and our common sense before deciding who and what to believe in. CONFIRMATION BIAS makes it very difficult to learn and retain facts that disagree with our personal biases.
Not understanding the failure to prosecute HRC, I listened to Comey’s testimony to Congress and how he answered Republican questions.
If there were a grand conspiracy, the existence of an investigation into the Steele Dossier would have been confirmed or leaked before the election, unleashing the storm of stories that appeared in January 2017.
FWIW, Mr. Mueller is entitled to keep the results of his investigation secret until he has finished questioning all of the witnesses – so he was some way to assess credibility.
Paul wrote: “Maybe I should be happy that someone still has faith in these folks, Mueller and his team do not deserve your faith.”
I think we should all consult a variety of sources and our common sense before deciding who and what to believe in. CONFIRMATION BIAS makes it very difficult to learn and retain facts that disagree with our personal biases.
I’d say that the email scandal shows that our government actually takes administrative procedure like FOI seriously, though the process is slow.
Paul: Peggy Noonan recently wrote a column on trust in our institutions:
“Realize there’s a difference between skepticism and cynicism, that one is constructive and the other childish.
Skepticism involves an intellectual exercise: You look at the grand surface knowing it may not reflect the inner reality. It implies action: If it doesn’t, try to make it better. Cynicism is a dodge: Everything’s crud, you’d be a fool to try and make it better, it’s all irredeemable and unchangeable.”
http://www.peggynoonan.com (May 31, 2018).
When the government’s internal watchdogs become more skeptical the people will become less cynical.
Claims that were made and accepted:
1) SOS Clinton had no emails.
2) No prosecutor would have brought a case against Clinton for violations of the National Security Act and obstruction of Congress regarding her emails.
3) Carter Page is a Russian agent.
4) Mueller’s investigation is just about finding the truth about Russian meddling.
5) The Obama FBI and DOJ were not politically biased.
6) Obama’s IRS honestly destroyed the IRS backup by accident after a year of a searching for it and under a non-destruction order. But there was not a “smidgen of evidence” of corruption.
Ron: To put it less cynically:
1) A search of the DoS email system turned up no account for HRC, and the initiators of the FOI were informed of this. The initiators were a liberal group with a new boss, and they chose not to pursue the issue. Others eventually noticed and did pursue it, ending HRC’s political career. (Justice?)
2) Comey informed irate Republicans that the FBI doesn’t monitor Congressional hearings determine if perjury was committed. If they had any complaints about the accuracy of HRC’s testimony under oath, they needed to file a complaint with the DoJ (just like the DoS IG). Such a complaint was allegedly made in the summer of 2016. An investigation of the CGI apparently also still exists.
3) Carter Page, a graduate of the Naval Academy, would have made a great recruit for the CIA, who could have planted him with GS in Moscow. As we know, the Russians were interested in recruiting him, or he could have been turned without being discovered. (See LeCarre) More likely, he has nothing to do with government intelligence services and swims with the sharks making a living trading business intelligence. Such people sometimes make mistakes and are compromised. Candidates receive confidential briefings. Campaign insiders often get appointed to high posts. Get a warrant and find out!
BTW: Bad searches are thrown out of court all the time. If Page wanted privacy, he shouldn’t have agreed to be an advisor for Trump.
Ron: continuing less cynicism.
4) The Mueller investigation is like an elephant; it is different things to different people. Read Rosenstein’s initial charter. Is he following it? (Some confidential amendments exist.)
https://www.justice.gov/opa/pr/appointment-special-counsel
5) Read Comey’s book, then you decide.
IMO, Mr. Comey’s greatest sin has been criticizing Trump after being fired. Many people are capable of informing the public about Trump’s flaws; Comey had little to add. Only Comey could defend the integrity of the FBI, something he claims to care about deeply His unnecessary personal attacks have destroyed his credibility.
6) IMO, our institutions failed badly with the IRS. If anyone needed to be impeached, it was Koskinen.
Find or pretend to find some new records. Immunize Lois Lerner and force her to publicly answer the questions of a well-prepared staff attorney, before letting incompetent Congressmen question her. (:))
3) Frank, the FISA warrant being filed on Carter Page with unverified allegations I would say indicates a serious breach of judgment and bias at the least. The three subsequent renewals of that FISA warrant, each legally requiring developments of corroborating evidence of seriousness of crimes like ties to terrorism, shows to me there was more than bias. As to what it was and who and how it evolved I am eager to learn and patient to find out. I strongly disagree that volunteering for a campaign adviser position should open one up to an implication of guilt and probably cause for an investigation by the state, especially one that would get leaked to the press.
The GOP freedom caucus today is advancing an impeachment of Rod Rosenstein. This will be the acid test as to where each congress person stands on the question of the Strzok-Comey-Rosenstein-Mueller being a “legitimate investigation” versus political op. The media will be in a frenzy. If they fail to stop the impeachment civil war?
Antony, it does not seem like the 12 GRU agents could be from the Dutch infiltration of the FSB’s Cozy Bear.
Do you have other information?
Frank, I don’t think Mueller’s team anticipates having to present any evidence so they would have no fear for of being accused of bringing bogus charges. It’s also amazing to me that nobody in the US IC seems to think it’s important to present any evidence to Trump, congress or the public.
No I don’t have other info, but both group apparently hacked the DCCC and DNC systems; anybody else could have too. The only real way to come up with factual names and individual actions of hackers would have been to daily identify their faces from the Russian CCTV in that University building next to the Red Square in Moscow.
Of course the FBI could simply have made up list of their most hated opponents – Occam’s razor.
The FBI indictment is pretty parallel to what was written here on CA including Crowdstrike’s (“Company 1”) failure to stop the hacking, even for many months till October 2016(!- page 12).
Wikileaks is nowhere to be found in this indictment: it is all about DCleaks and Guccifer 2.0 not read or taken serious by the masses of US voters. Anyway, they were quite capable to make up their own minds months afterwards at the election, seeing through dirt kicked up on both candidates.
Ron is correct.
The CCTV images taken by the Dutch in 2015 (or 2014?) where from Cozy Bear (APT-28) personnel, who work for the SVR (not FSB as some US sources have incorrectly stated). Those people are different from the Fancy Bear / APT-29 (GRU) crew, who are alleged to have hacked the DNC in April/May 2016.
The Ducth AIVD/MIVD team warned the USA about hacking of DNC, Stated Dept. and (apparently) White House computers by Cozy Bear in 2015.
Around that time they (AIVD/MIVD team) managed to get access to a Cozy Bear Command & Control server in their investigation into hacks of EU (and NL) targets (since 2014). At the C&C server they apparently saw traffic incoming from victim computers (laptops, workstations or even servers) located in the USA. Some were identified as using US Gov IP ranges and others as belonging to the DNC.
The US Gov & FBI was informed by the Dutch in summer 2015. US Gov took action to remove the malware & close down connections (as all IP addresses would have been known).
The FBI informed the DNC several times via phone in 2015 and in person in January 2016 (SA visited DNC HQ, because DNC continued to openly disbelieve that the warnings came from FBI, or so they claimed). No action was taken to remove Cozy Bear malware (as far as we know) until CrowdStrike was called in late Apri 2016 (when they found Fancy Bear malware, the old stuff was a side issue).
Ah no. The US Intelligence community probably simply knows the team at the GRU from other sources. The indictment links the conclusions & statements of what happened as determined by CrowdStrike with known agents of the GRU. Person X is know to be a Dev/Tester so he is assigned that role in the indictment. etcetera.
To what extent the identification of unknown actors (from CS story) with actually known people in GRU are really correct is yet to be seen.
Ron wrote: “I don’t think Mueller’s team anticipates having to present any evidence so they would have no fear for of being accused of bringing bogus charges. It’s also amazing to me that nobody in the US IC seems to think it’s important to present any evidence to Trump, congress or the public.”
I suspect that Mueller’s team risks being disbarred for making misrepresentations in court about evidence. Perhaps jddohio will comment.
The Russians have hired a US attorney to represent them in the previous case Mueller case and he requested evidence. The prosecutors demand assurances that the defendants would actually show up for a trial before handing over evidence.
I presume that every step of this process has been carefully considered. I doubt that Mueller has left himself (and his country) open to the potential embarrassment of not being able to back up their charges with evidence.
Frank commented: “I presume that every step of this process has been carefully considered. I doubt that Mueller has left himself (and his country) open to the potential embarrassment of not being able to back up their charges with evidence.”
Frank, I think I agree with your assessments except for your perceived chance that the GRU is going to come to the USA to be prosecuted by Mueller’s team. There more risk to Mueller of being struck by lightning. Historians may be able to get it by FOIA in 50 years if America had not become a rotted socialist H-hole by then.
Our host has another line of speculation on this name / action list, based on intel coming from inside Russia; see https://twitter.com/ClimateAudit/status/1019621809031909376
The Bell article pointed to by our host brings up a lot of questions.
1) Is Kozlovsky admitting he was Guccifer 2.0?
2) If he claiming he supplied WL with DNC and Podesta goods?
3) Why did he follow FSB directions if he is part of a criminal hacker group?
4) Why is he confessing?
5) Why is he charged with treason?
6) Why is there a news blackout on this in the US?
7) If he is so brilliant and is telling the truth why didn’t he retain a DNC and or Podesta document unpublished to present as evidence of his accomplishment?
8) If he was Guccifer 2.0 why did he use a computer registered to Warren Flood?
In regard to the Dutch IC catching the Russian government hackers on camera and presenting to the FBI, this would have put that evidence in the hands of the same counter-intelligence clan that is implicated in Spygate. And whereas we now know that there was a free flow of information from the Bruce and Nellie Ohr connection of the DOJ counter-intelligence with Fusion GPS, Hillary would have known of the ironclad Russian evidence regardless of Crowdstrike’s assessment. This may be why the FBI could be excused by the US IC for being disinterested in taking possession of the DNC server.
The finding of the Russian hack on Hillary For America is concurrent with the entry of Paul Manafort into the Trump campaign. Hillary’s intelligence officer, Sydney Blumenthal, would certainly have known of Manafort’s past connections to the Putin-friendly Ukranian regime. Tony Podesta is thought to have used Manafort in the Uranium One deal in 2010.
It seems clear now how Hillary would want friends at the US IC to open a counter-intelligence operation on her behalf (and that of America) against Trump.
Ron: Mueller can’t be sure what a judge will demand of him if a defendant appears committed to going to trial.
It isn’t likely, but the Russians could chose to risk an unimportant agent to discredit Mueller’s evidence (you suggest may not exist) and sow dissent in the US during a trial. The USSR almost certainly has sent fake defectors to us before to endure years of confinement and questioning.
We agree that Mueller will have prepared for all reasonable contingencies.
FBI director in Aspen: “Chinese espionage the most significant treat facing us”. Also not too interested in questioning those 12 (ex) GRU personnel in Russia. (Putin asks a tit-for-tat questioning of various characters in the US – too much to swallow)
Phishing is the way to deceive users by using medium likes phone calls emails and many tools and take a credential information like password, credit card details etc. To prevent phishing install a BitDefender antivirus.
7 Trackbacks
[…] https://climateaudit.org/2018/03/24/attribution-of-2015-6-phishing-to-apt28/#more-23668 […]
[…] https://climateaudit.org/2018/03/24/attribution-of-2015-6-phishing-to-apt28/#more-23668 […]
[…] https://climateaudit.org/2018/03/24/attribution-of-2015-6-phishing-to-apt28/ […]
[…] https://climateaudit.org/2018/03/24/attribution-of-2015-6-phishing-to-apt28/ […]
[…] https://climateaudit.org/2018/03/24/attribution-of-2015-6-phishing-to-apt28/ […]
[…] The first article linking the DNC hack to APT28 spearphishing by SecureWorks (here) in June 2016. Secureworks had been tracking APT28 spearphishing for some time through their bitly links. They provided two examples linking respectively to the malicious domains: accounts-google[.com and googlesetting[.com. I’ve looked at both, but will discuss only the latter in this note. These domains were previously discussed at CA here. […]
[…] https://climateaudit.org/2018/03/24/attribution-of-2015-6-phishing-to-apt28/ […]